Overview
This is part 2 in a multipart series on how macOS devices are managed by Intune. In part 1 we look at the history of macOS management. In part 2 we look at how macOS handles MDM with Intune. Finally, in part 3 we look at Company Portal’s role in macOS management.
Intro
We will be focusing on macOS’s response to MDM commands, specifically InstallProfile. There are a number of commands like InstallApplication, RemoveProfile and more. If you are interested in a post on those, comment below. Let’s assume that we have a device enrolled into Intune using ADE. Additionally, we will focus on the in-market functionality of MDM, and not DDM, or Declarative Device Management, as macOS will support this as of Sonoma, however this is still a maturing management framework.
Let’s Talk Configuration Profiles
At its most basic level, Configuration Profiles are XML documents. These files are delivered to the client and ingested by a service inside of macOS. For the most part, you will never interact with profiles directly. However, it is good to know the structure of Profiles at a high level. Below is an example of a Profile used for SCEP from Apple’s Configuration Profile Reference documentation, here. This documentation includes details on a Profiles structure and important keys like PayloadType, PayloadContent, PayloadOrganization, among others.
<?xml version=”1.0” encoding=”UTF-8”?>
<!DOCTYPE plist PUBLIC ”-//Apple Inc//DTD PLIST 1.0//EN” ”http://www.apple.com/DTDs/
PropertyList-1.0.dtd”>
<plist version=”1.0”>
<dict>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadUUID</key>
<string>Ignored</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadIdentifier</key>
<string>Ignored</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadContent</key>
<dict>
<key>URL</key>
<string>https://scep.example.com/scep</string>
<key>Name</key>
<string>EnrollmentCAInstance</string>
<key>Subject</key>
<array>
<array>
<array>
<string>O</string>
<string>Example, Inc.</string>
</array>
</array>
<array>
<array>
<string>CN</string>
<string>User Device Cert</string>
</array>
</array>
</array>
<key>Challenge</key>
<string>...</string>
<key>Keysize</key>
<integer>1024</integer>
<key>KeyType</key>
<string>RSA</string>
<key>KeyUsage</key>
<integer>5</integer>
</dict>
<key>PayloadDescription</key>
<string>Provides device encryption identity</string>
<key>PayloadUUID</key>
<string>fd8a6b9e-0fed-406f-9571-8ec98722b713</string>
<key>PayloadType</key>
<string>com.apple.security.scep</string>
<key>PayloadDisplayName</key>
<string>Encryption Identity</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadOrganization</key>
<string>Example, Inc.</string>
<key>PayloadIdentifier</key>
<string>com.example.profileservice.scep</string>
</dict>
</array>
</dict>
</plist>mdmclient
In macOS the process responsible for MDM communications is mdmclient. Let’s take a look at the man page.
It’s pretty empty 😊. While there is not much here on the surface, mdmclient is an integral part of the management story on macOS. The processes’ sole purpose is handling MDM commands and messaging via XPC to other system services to gather information or apply an intended action. The process has an instance as a LaunchAgent (com.apple.mdmclient.agent.plist) and as a LaunchDaemon (com.apple.mdmclient.daemon.plist). This allows for the binary to respond to user requests and device requests respectively.
Demo Time
In the following scenario we have an IT Admin that needs to disable the ability for users to use >Console Login at LoginWindow for their Macs.
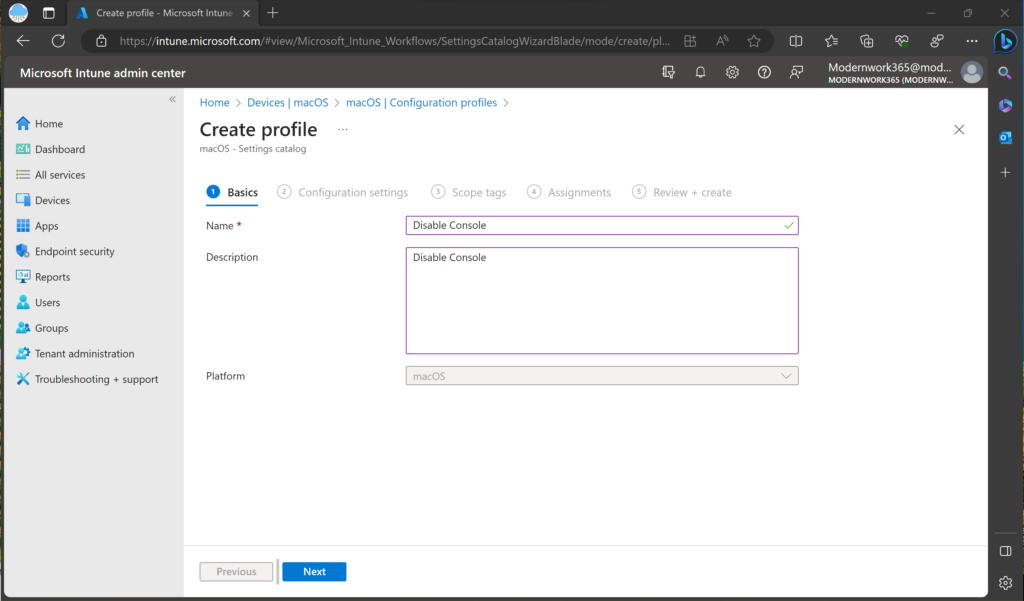
Opening Edge we start in the Intune Admin Center>Devices>macOS>Configuration Profiles>Create>Settings Catalog. We will set the name and description of the Profile to something indicating what we are managing.
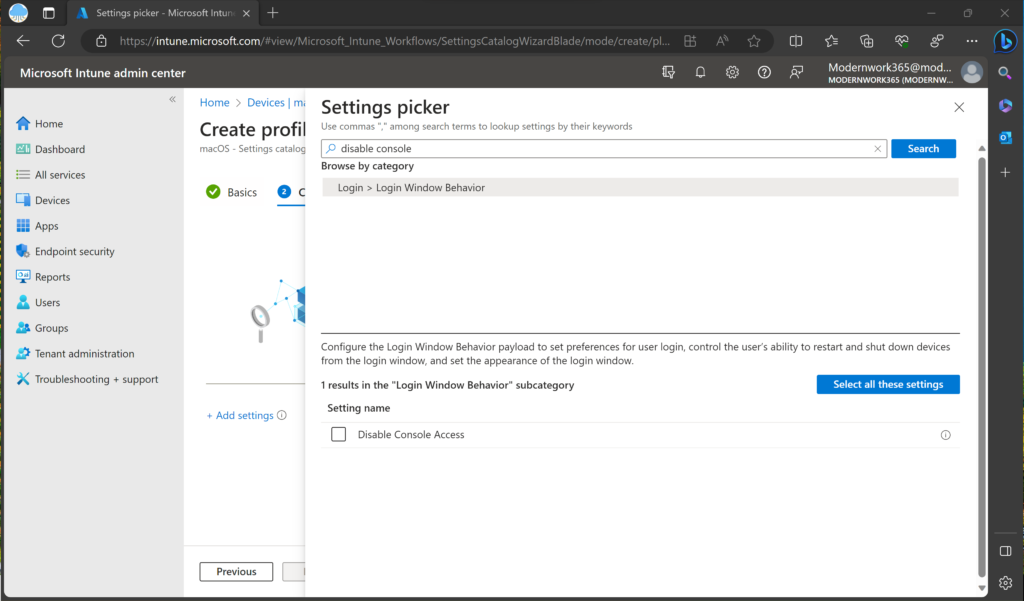
Next using Settings Picker, we will search for “Disable Console Login”, select the payload, and enable it.
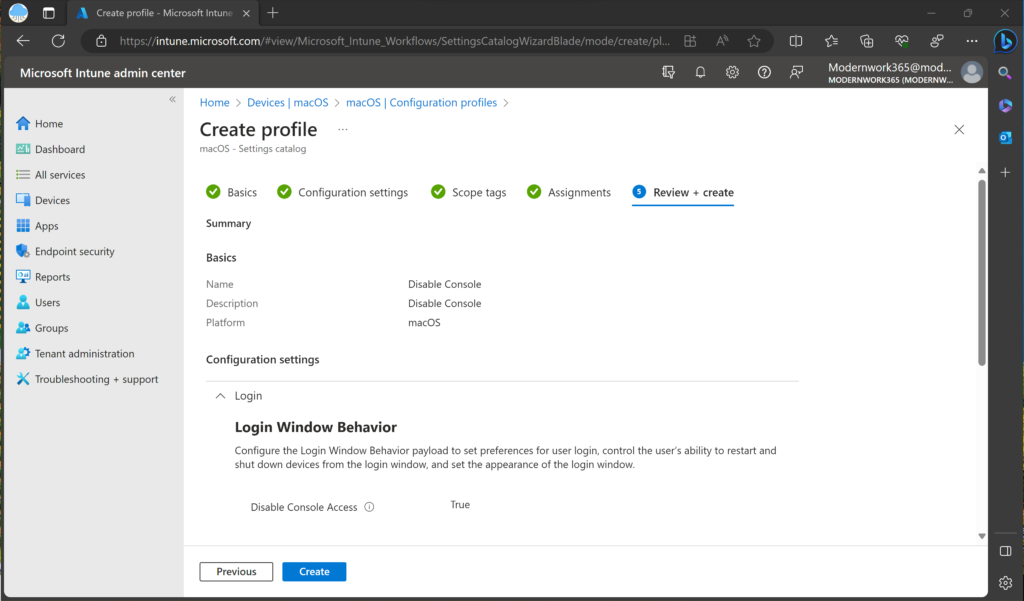
We will set Scope Tags, an Assignment, and finally save and deploy the Profile by clicking Create.
Console
For our scenario I have installed the MCX Debug Profiles from Apple’s Developer Portal to get a bit more detail on whats going on under the hood. On my Intune managed Mac using Console I set the Logging Subsystem to show events from com.apple.ManagedClient.
Notice around 12:41 the client receives a InstallProfile Command that Intune issued when we saved the Profile. The Profile that is deployed contains the LoginWindow Preferences we set in Intune.
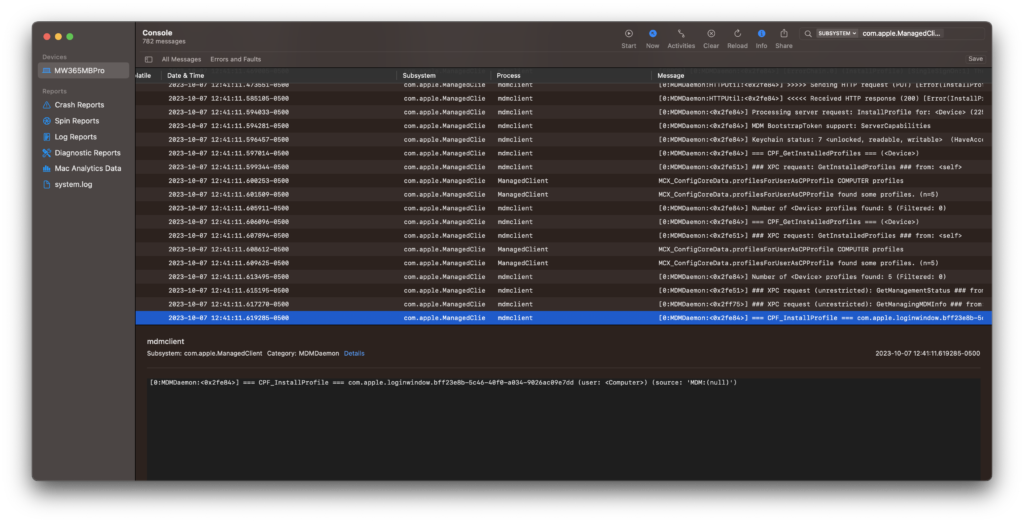
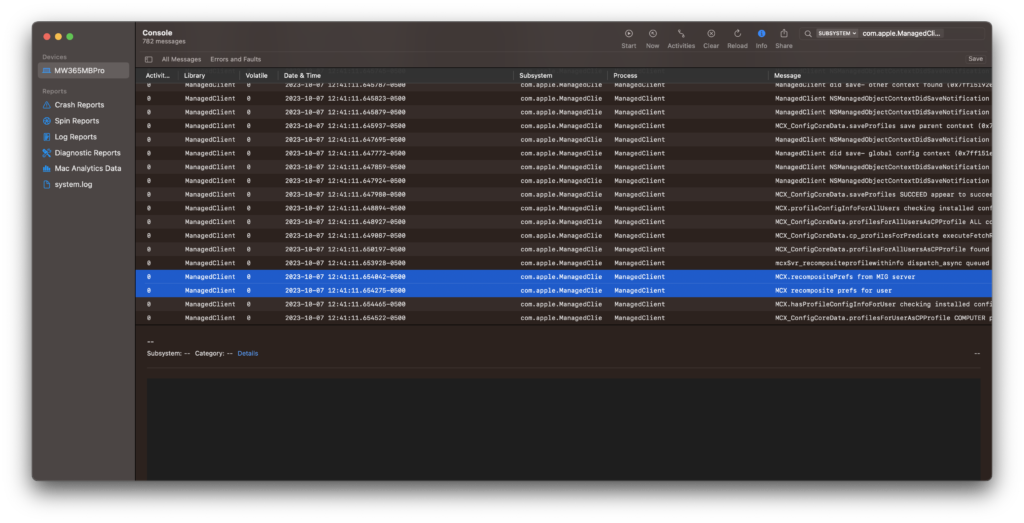
The mdmclient installs the Profile, and then triggers the MCX Compositor, part of ManagedClient.app to refresh and merge preferences for the user and computer.
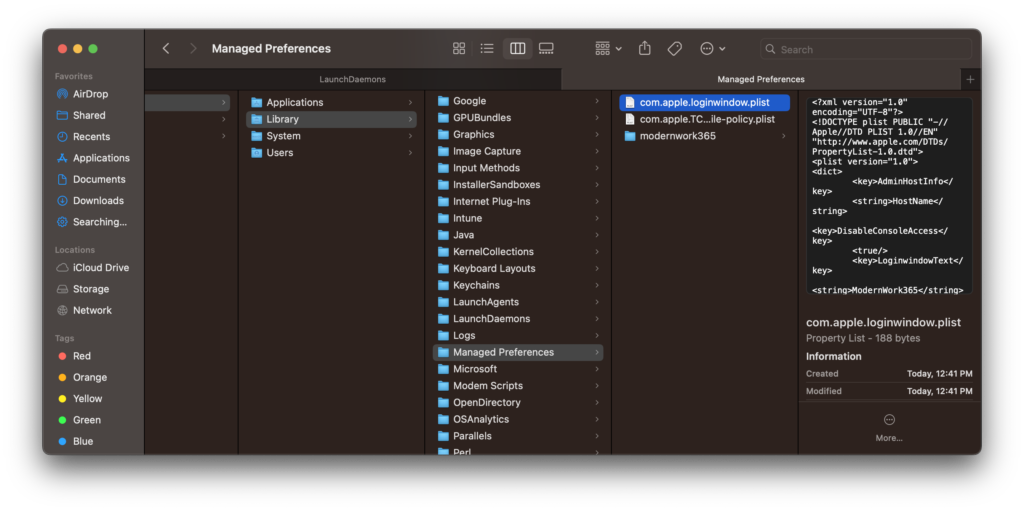
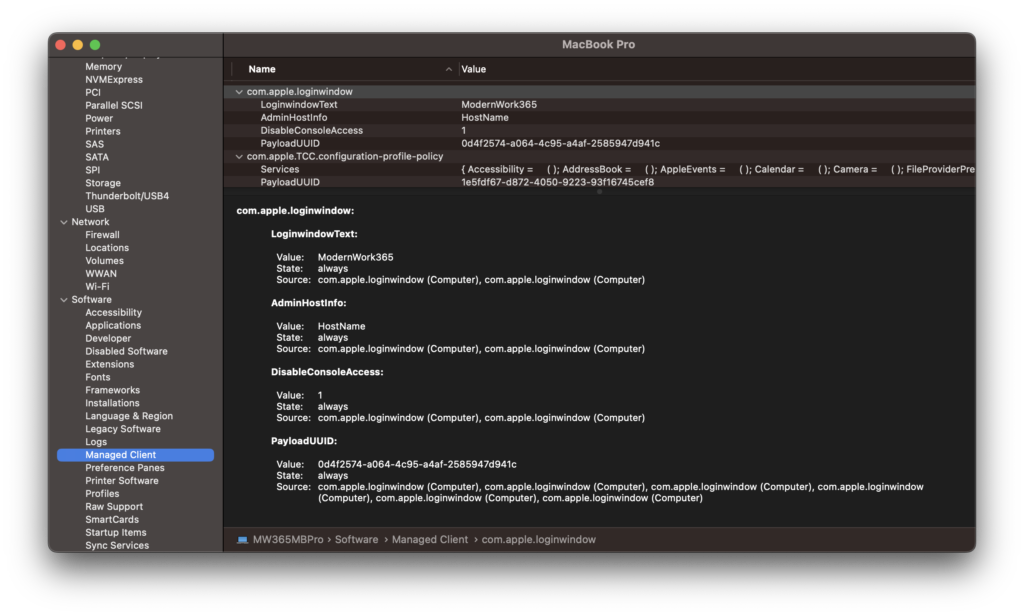
At this point we can check out a few locations to see the effects of the settings. MCX settings live in /Library/Managed Preferences. Looking at this location we can see com.apple.loginwindow.plist.
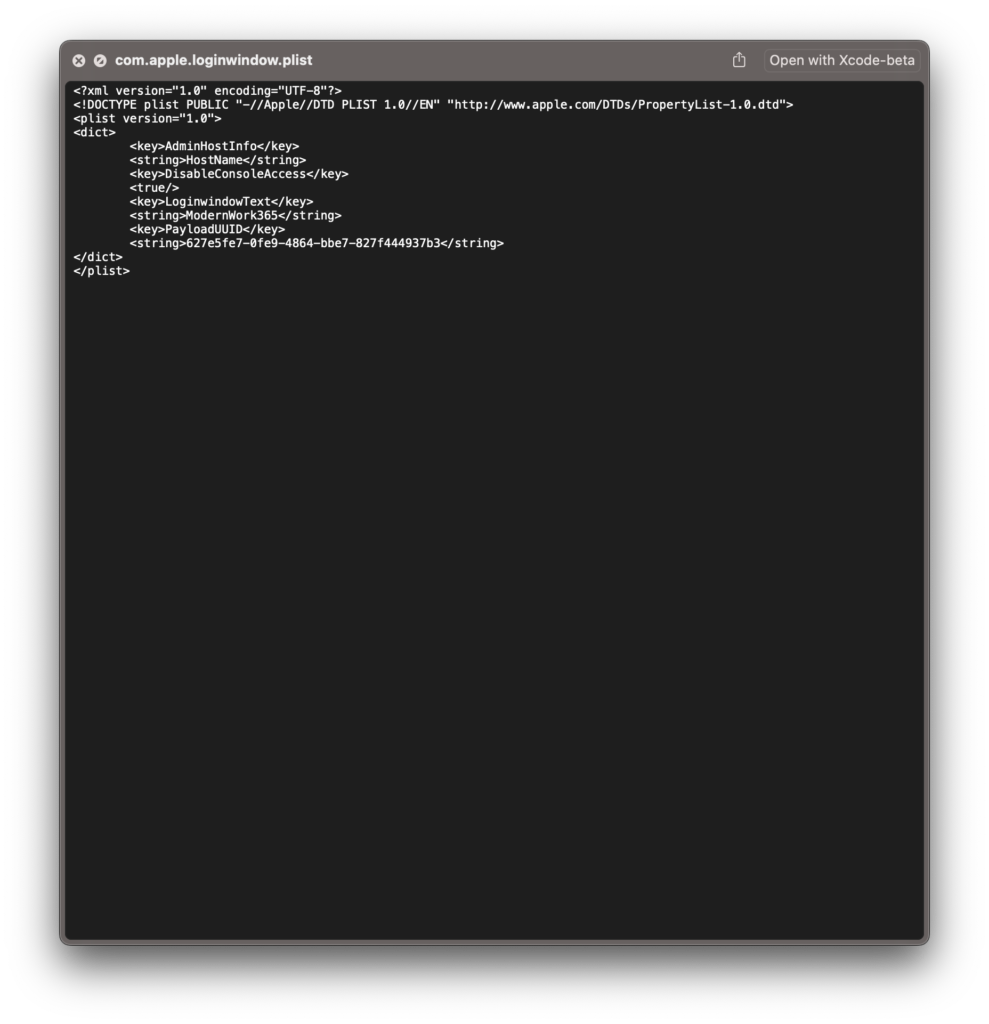
Using QuickLook we can see a key called DisableConsoleAccess is set to True. Additionally, you can see the result of the MCX Compositor here as other Profiles deployed to this Mac that have other LoginWindow settings.
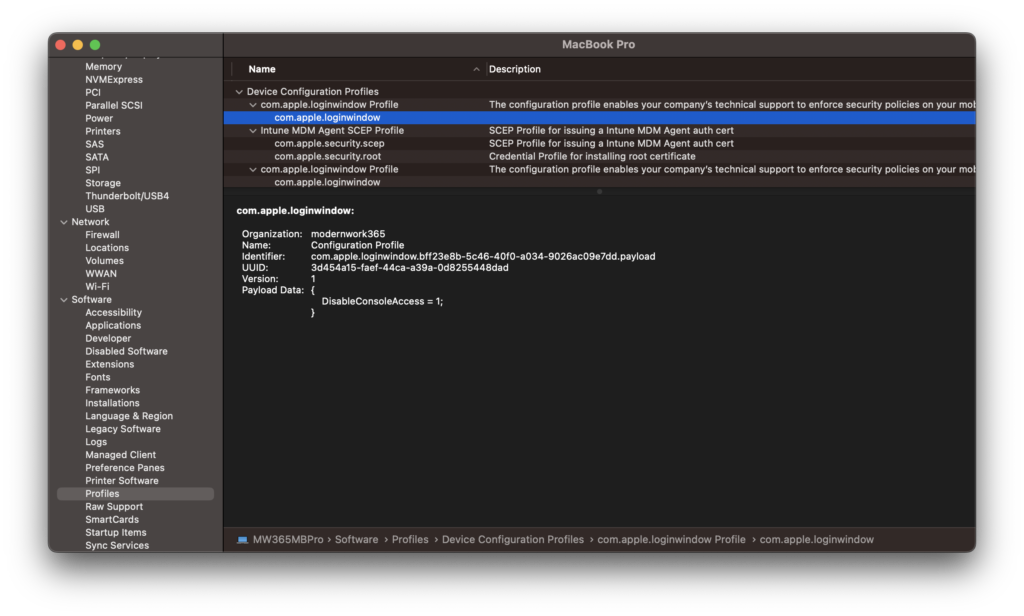
Using System Information.app both the Profiles and Managed Client sections show the DisableConsoleAccess now managed.
Thats It!
Common Troubleshooting tips with Profiles and MDM
- Ensure your users are licensed with an Intune license.
- Ensure the number of devices a user has enrolled does not exceeds an enrollment restriction.
- Make sure your enrollment restrictions are not blocking macOS enrollment.
- Enrollment and profile failures can be due to APNS being blocked on your network. Check out this kbase article here for details.
- You cannot inspect APNS traffic, nor can it require authentication to a proxy. APNS traffic needs to be excluded from authentication and SSL decrypt polices on your proxies or firewalls.
- The Property Lists in /Library/Managed Preferences/ can be trashed! If you experience issues with MCX Compositing not rendering settings correctly you can simply trash the preferences. They will regenerate upon logout/logout, shutdown/startup.
- Install the MDM / MCX debug profiles from Apple’s Developer site when troubleshooting MDM issues.

