Collection Cloud Syncing in Microsoft Configuration Manager provides “cloud value” to Configuration Manager when its “Cloud Attach” (For a quick reminder of what Cloud Attach is click here). Its purpose is to provide a mechanism to export the results of a Collection to a Entra ID Security Group. This feature, while initially introduced in 1906 release of ConfigMgr, has recently been given some significant updates so I felt it would be helpful for a deep dive into how you can use this feature and what to check into when things go south. 🙂
So why should I be syncing Collections results to the Cloud?
Most organizations have existing investments with Microsoft Configuration Manager, and while Entra ID has rich set of grouping capabilities (Dynamic Device and User Groups) there are a lot of business processes entrenched in the complex logic of Collections. In your journey to modernize, these may be too complex, or not possible to recreate in Entra ID. This is where Cloud Sync for Collections provides a bridge, enabling you to deploy modern workloads in Intune to a scope defined in ConfigMgr.
Example Scenario
For example, let’s say you have a Collection where membership is dependent on if MSSense.exe (XDR) is running on your Secure Access WorkStations (SAW). Further you would like to apply Policy from Intune on these systems. (I picked this example as currently you cannot group based on this criteria in Entra ID, further hopefully your SAWs don’t have open internet access 😉)
Getting Started in Entra
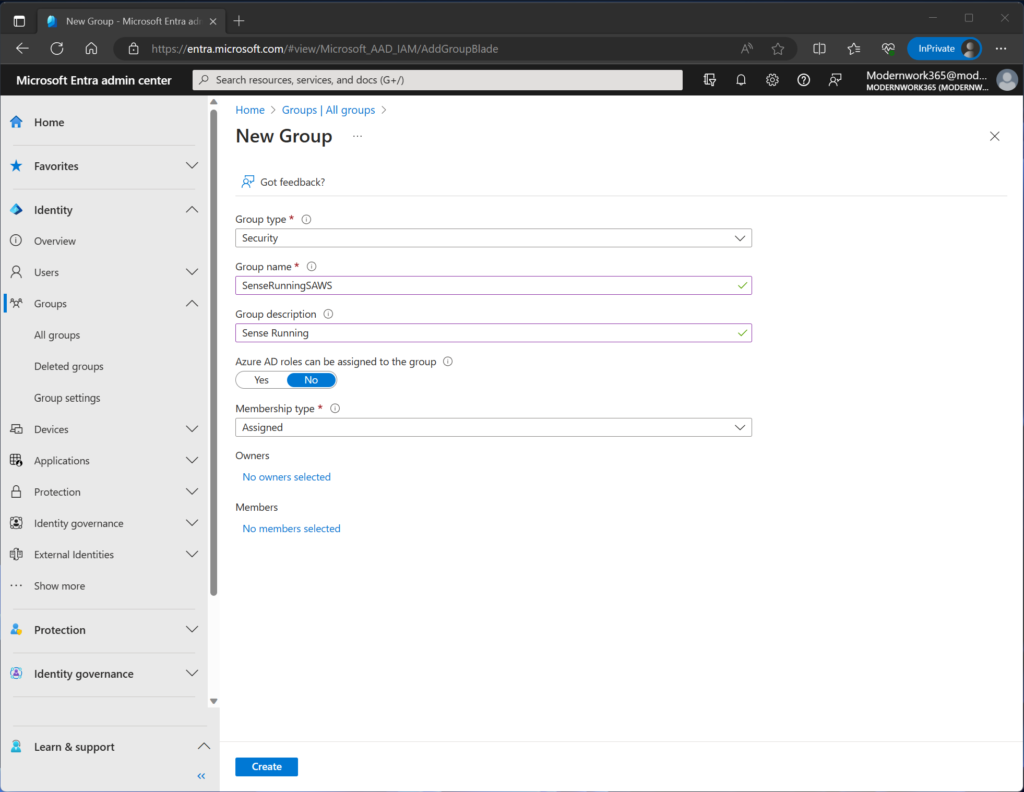
Open a browser and navigating to entra.microsoft.com > Groups > Create Group.
Next set the Group type to “Security” along with a “Group name”, “Group description”, and finally set the “Membership type” to “Assigned”.
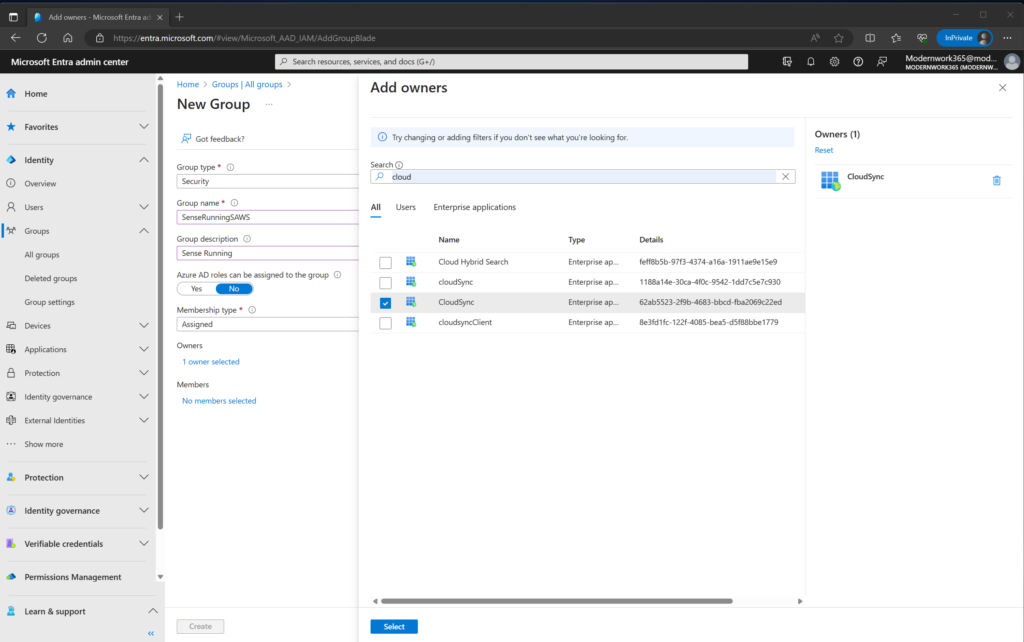
Next select “Owners” and add select the App Registration. Below I have already setup Cloud Attach and Cloud Management, and I will be using an App Registration called “CloudSync” created when I enabled “Cloud Management”.
This ensures that the Service Principal has the ability to CRUD objects inside the group.
CRUD Stands for Create, Read, Update, Delete
Up Next: ConfigMgr
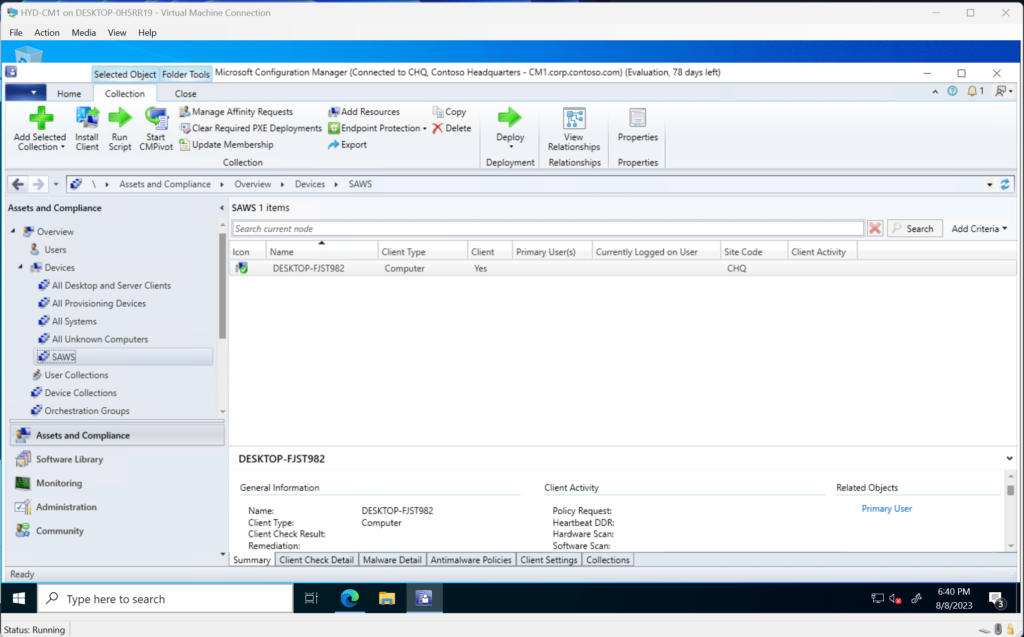
Pivot over to the Configuration Manager Console, Assets and Compliance > Devices Collections, and we find the collection that we want to sync. For my scenario, “SAWS”.
Right click on the Collection and select Properties > Cloud Sync > Add.
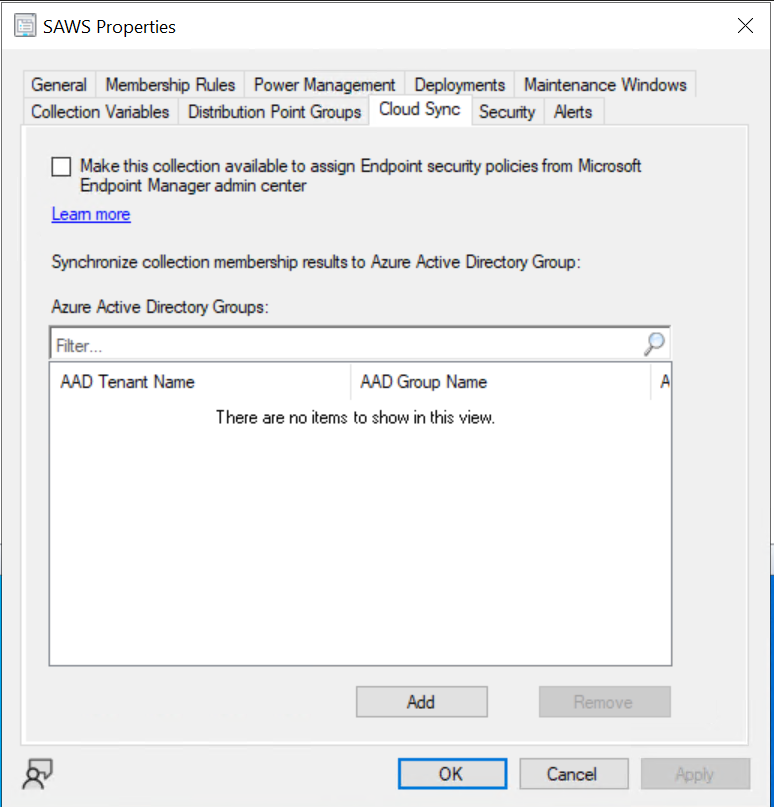
Note the “Make this collection available to assign Endpoint Security Policies form Microsoft Endpoint Manager Admin Center” for targeting Security workloads….😉
Next, we search for the Entra ID Group created early, “SenseRunningSAWS” click “OK” to close the dialog, and “Apply”, and “OK” to close the Collection Properties.
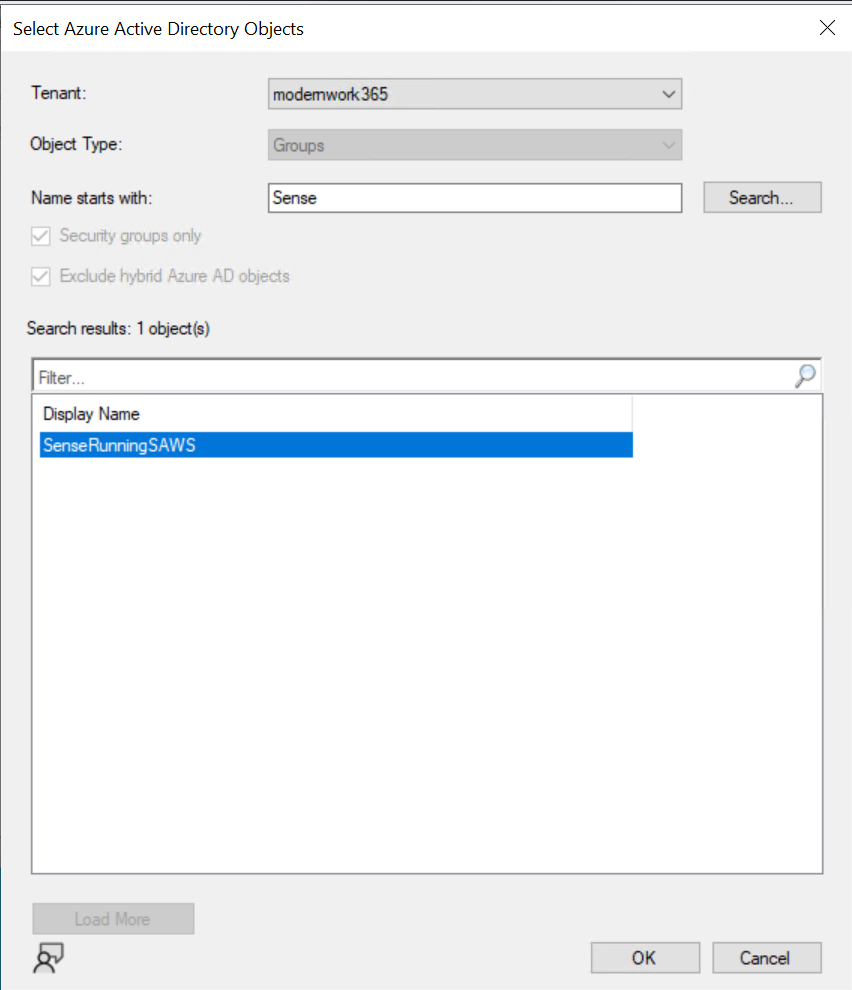
As The collection eval kicks off, hop over to the Monitoring > Collection Cloud Sync > Device Collections to check the status.
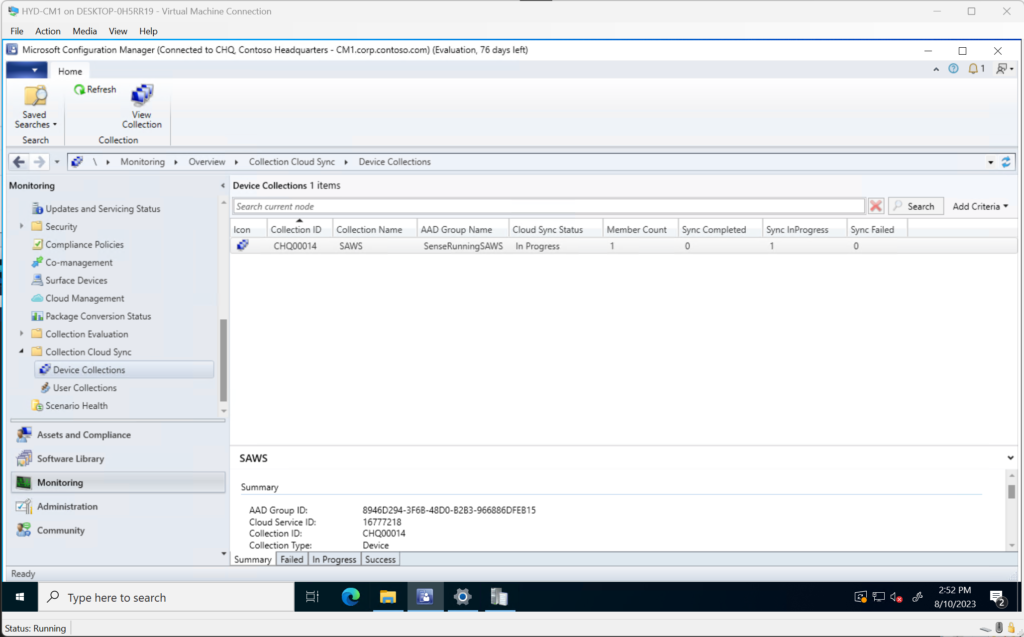
Once ConfigMgr completed the sync, navigating back to the Entra Admin Portal we can see the object added to the Security Group. We are now free to use this in the Intune Admin Center to deploy what you need.
Further Digging:
Navigating to the logs directory on the Primary Site, we find SMS_AZUREAD_DISCOVERY_AGENT.log. If we use CMTrace to view the log, we see the Entra ID device Object being added to the Entra ID Group Object.
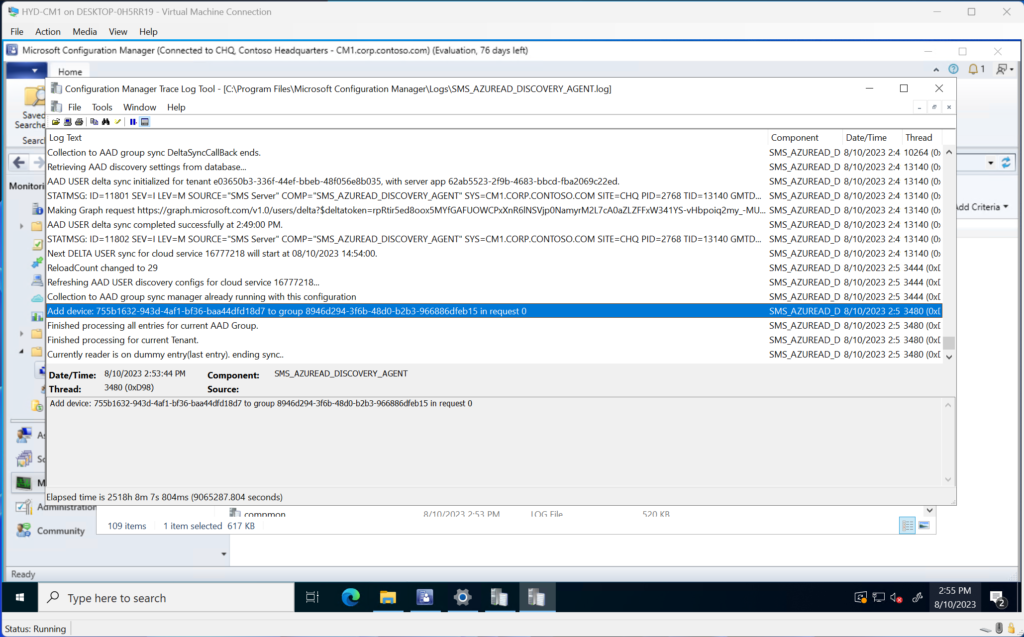
Final Thoughts
Syncing Collection results to Entra ID Groups is a powerful mechanism to help address some of the complexities for grouping devices or user in Entra ID. This enables you to continue to use these grouping metaphors to bring groups of devices or users into Intune so you can use target modern workloads with them.
Configuration Manager Notes:
- Configuration Manager needs to be at least 1906 to support Cloud Syncing to a Security Group. But to get all the new goodness, get up to the latest version. =)
- Cloud Management (2303) or Tenant Attach (pre2303) needs to be configured.
- Entra ID (Azure AD in console) Discovery should be enabled.
- Use Monitor Node for details on sync issues.
- For more detailed information see the SMS_AZUREAD_DISCOVERY_AGENT.log.
- The previous version of this feature logged to CollectionsAADGroupSyncWorker.log. I was unable to find this in newer versions of ConfigMan, thus this blog 🙂
- Always make changes from the Configuration Manager Console, not Entra ID. Changes are not reflected back to the Collection. This has not changed with the updated Feature.
- Both user and device objects are supported.
- Now with PS Support: Set-CMCollectionCloudSync
- Microsoft Docs on Collection Cloud Sync, here
Entra ID Notes
- You can locate the Entra ID Object ID of the device and group in question in the Entra Portal.
- Check the Audit logs in your Security Group for any issues with group membership CRUD.
Endpoint Notes
- The device needs to have a relationship with Entra ID, either Hybrid Entra ID Join, or Entra ID Joined.
- If the Device is not Entra ID Joined or Hybrid Join you will get an error in the console about the device object not existing in Entra ID.
- Use dsregcmd /status to check into devices join status.
- Support for Co-Managed using Entra ID Join, Co-Managed Hybrid Entra ID Join are both supported scenarios.