Microsoft Defender For Endpoint (MDE) has a number of capabilities to enforce settings management across your estate. Depending on the platform, MDE can be managed via wide range of mechanisms:
-
- Group Policy Objects (GPO)
-
- Mobile Device Management (MDM)
-
- MDE Attach for Windows Servers and Client
-
- Configuration Manager
-
- mdatp_managed.json
-
- shell scripts via Intune Management Extension (IME)
-
- Extension Attributes (Jamf)
For non-Windows machines, most organization are using a mix of configuration management (Linux) and MDM (macOS) tooling to manage MDE Settings. This can cause friction within organizations as Security Engineers need to rely on End User or Server Teams to manage configuration on non-Windows platforms, where the have some ability today in Intune to manage Windows estate in MDE Attach. Fortunately, MDE Attach for macOS and Linux is coming this year to give back some control to your Security Team.
Recap on what is MDE Attach
Initially announced in 2021, with general availability (GA) in 2022, Security Settings Management, or MDE Attach is a capability to manage MDE Settings via a dedicated management channel.
Scenarios where this can be used.
-
- Organization wanting all MDE Settings to “come” directly from M365D Portal and not rely on other organizations outside of Security.
-
- Linux Servers supported by MDE.
-
- macOS devices using Jamf or a 3rd Party MDM
-
- Decentralized organizations where there is little configuration management, or separate teams managing portions of IT infrastructure.
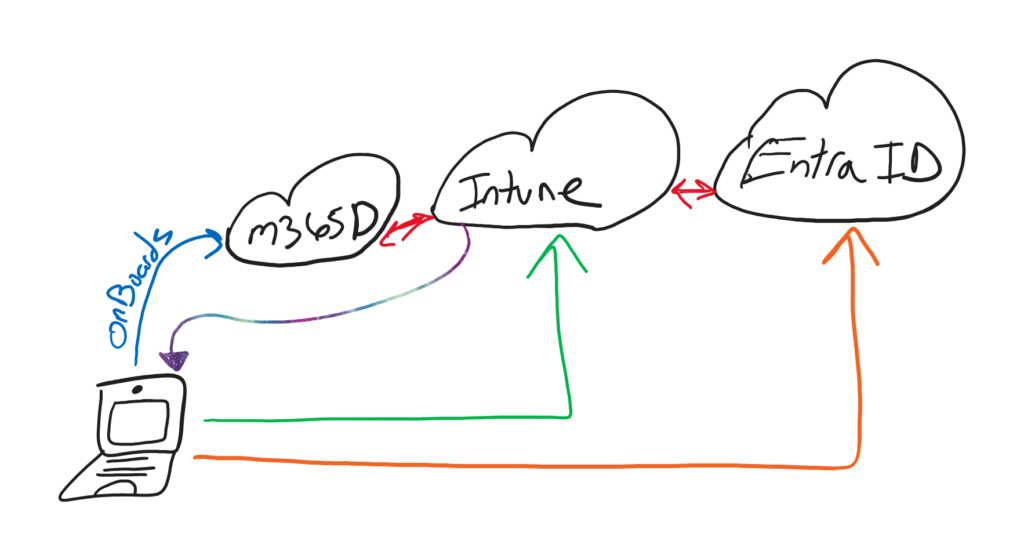
How MDE Attach Works
MDE Attach is a very straightforward process. At a high level:
-
- A Client is onboarded to M365D using a supported Onboarding Method.
-
- The MDE Agent queries the device for existing MDM Enrollment, and relationship with Entra ID.
-
- If one is found, this is used, if not the client initiates a special type of Entra Join called Synthetic Registration.
-
- Intune deploys policy and the client ingests the policy via SenseCM, a component of MDE.
Synthetic Registration is a trust between the client and Entra ID. It’s simply used to get policy from Intune.
Testing out MDE Attach
Starting with some device already onboarded in the M365D Tenant, we will want to ensure that the M365D and Intune are configured correctly. Open a browser and navigate to security.microsoft.com > Settings > Endpoints > Advanced Features and toggle the “Microsoft Intune Connection” on.
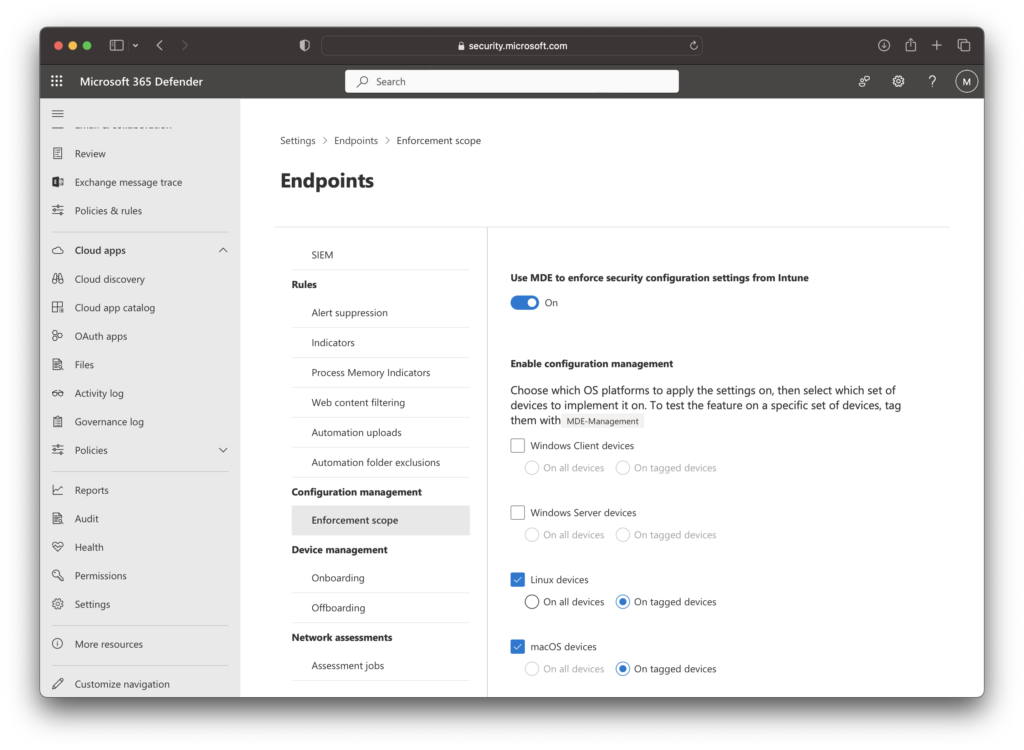
Under Settings > Configuration Management > Enforcement Scope enable “Use MDE to enforce security configuration settings from Intune”. Under macOS and Linux enable your deployment approach “on tagged devices” or “on all devices”. For the purposes of demonstrating, we will use device tags.
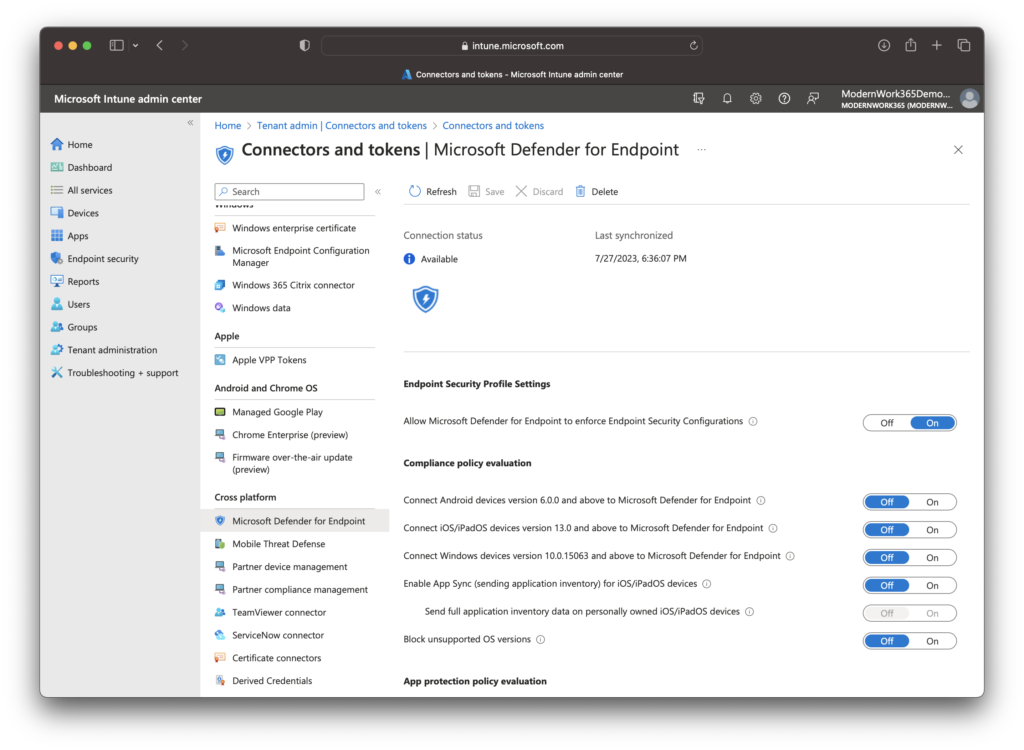
Hop over to intune.microsoft.com > Tenant Administration > Connectors and Tokens > Microsoft Defender for Endpoint and enable “Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations”.
Getting Started – macOS and Linux
MDE Attach is supported on macOS on agent version 101.23052.0004 or higher. Depending on how you are updating your macOS devices, this may already be taken care of. On the test machine I am running macOS Ventura (13.5), and have installed MDE, and have onboarded the system. Additionally, the device has been tagged in the M365D portal with “MDE-Management”.
MDE Attach is supported on Linux on agent version 101.23052.0009 or higher. Depending on how you are updating your Linux Servers, this may already be taken care of. I am running Ubuntu 22.04.2 LTS, have installed MDE, and have onboarded the system. Additionally, the device has been tagged in the M365D portal with “MDE-Management”.
Policy
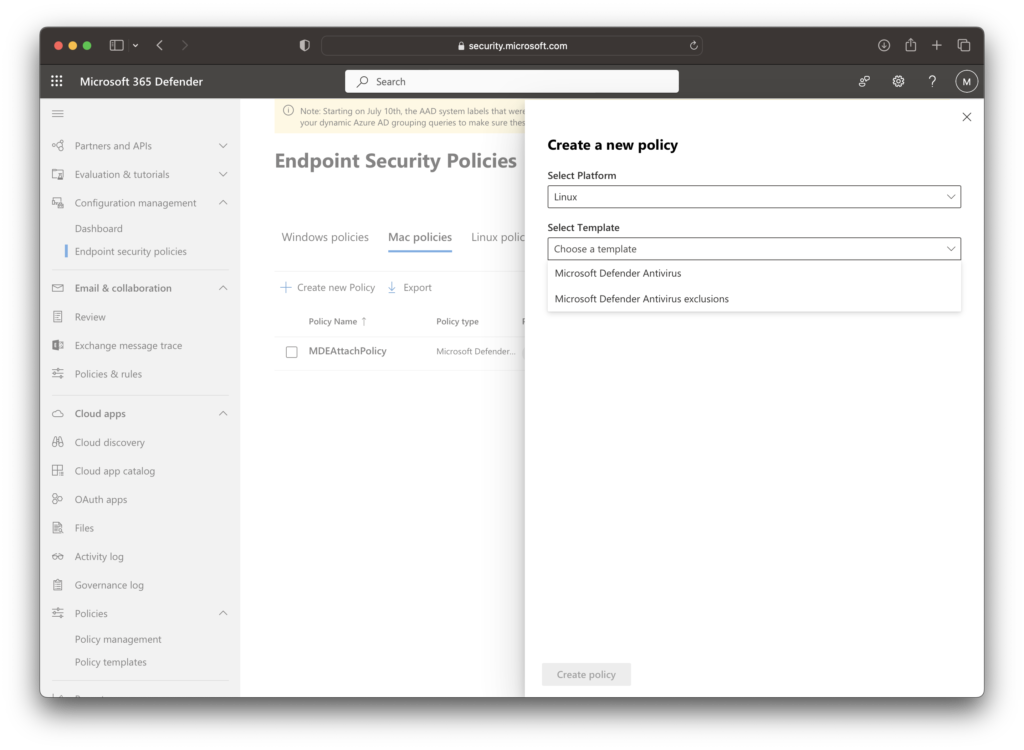
Up until the Public Preview of this, Security Engineers were limited to using the Intune Admin Center to author Policy. With the additional OS support, You can now author policy directly in the M365D Portal. Navigate back to security.microsoft.com and select Endpoints > Configuration Management > Endpoint security policies > and click “Create Policy”. The “IT Pro Journeys” are very similar in both macOS and Linux as of this posting. For brevity, we will focus on policy creation for Linux.
-
- On the flyout select Microsoft Defender Antivirus under “Select Template”.
Name the policy, and a description.
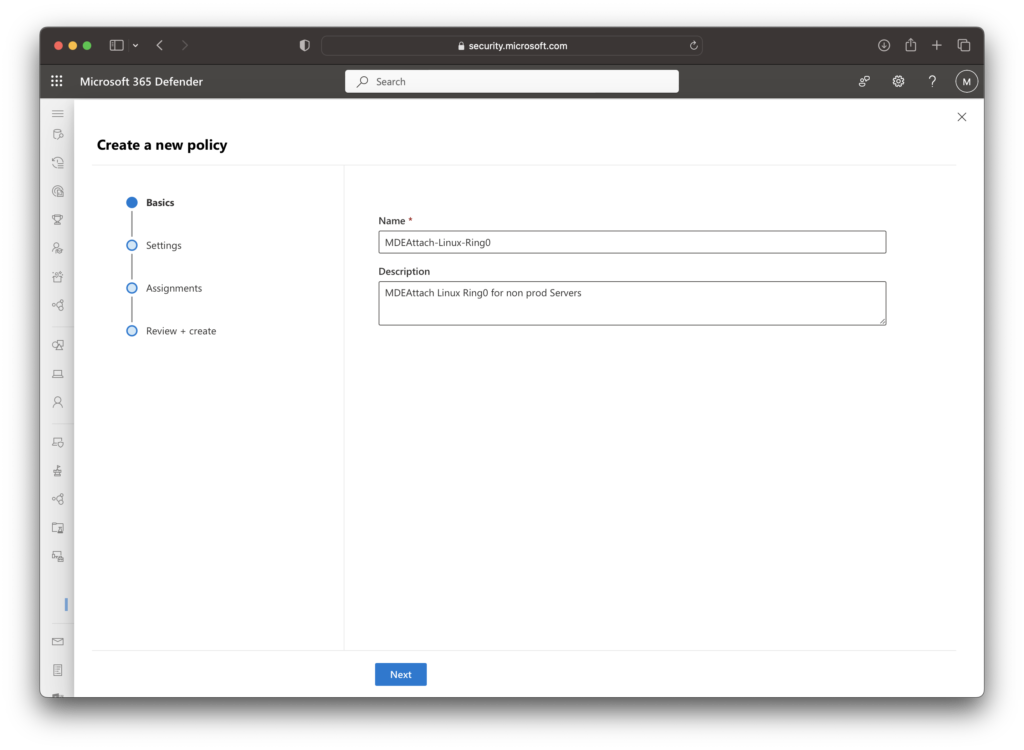
Select the settings you want to manage per your organization’s security requirements.
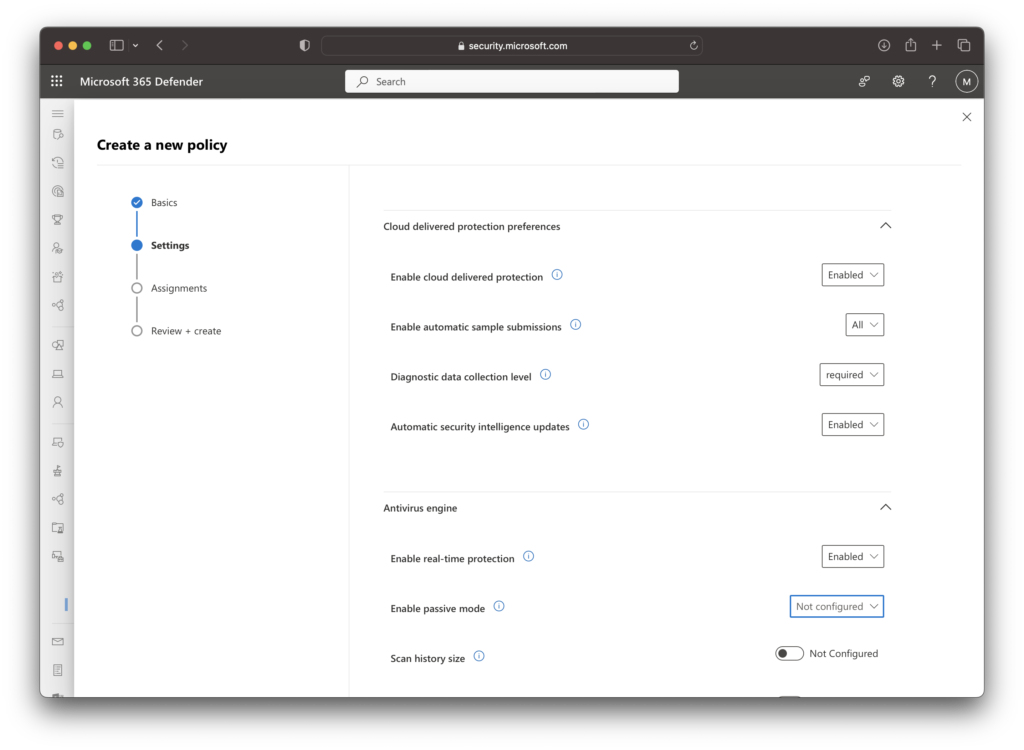
For the purposes of this posting, I used Device Tags as my sandbox only had a few systems. Depending on the deployment method, use Entra ID Dynamic Device Group for a controlled rollout.
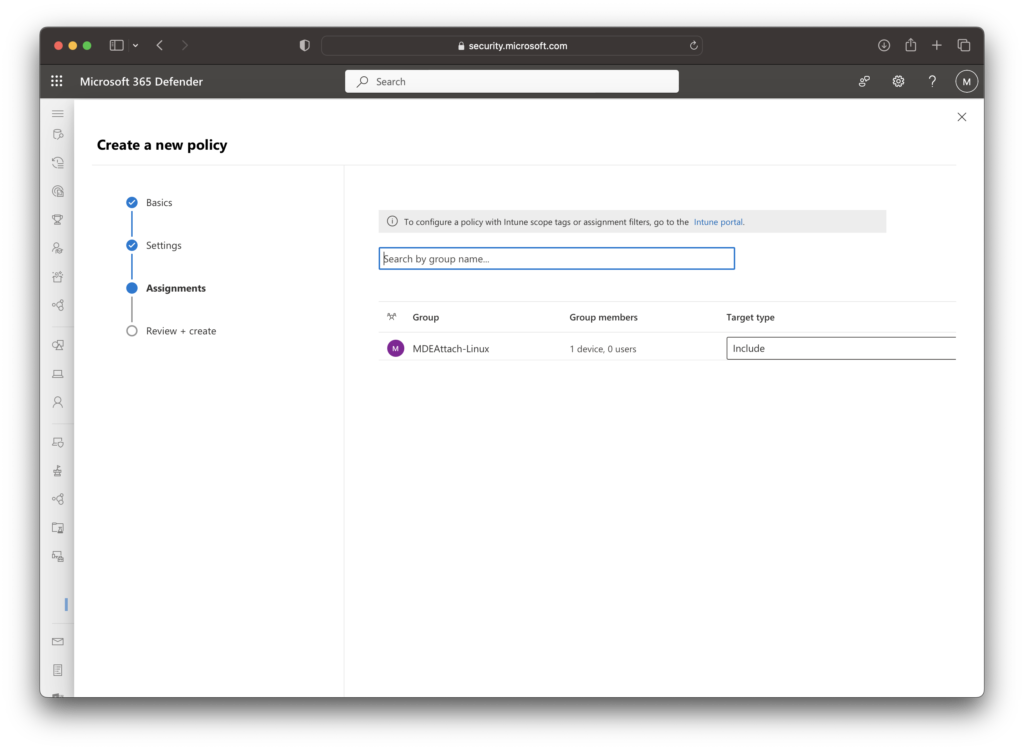
Verify your settings and click “Save”.
Client Side
Once the policy is saved and targeted, we can switch over to our test systems. On the Ubuntu VM doing a mdatp health resulted in the Managed key applying the settings defined in the policy.
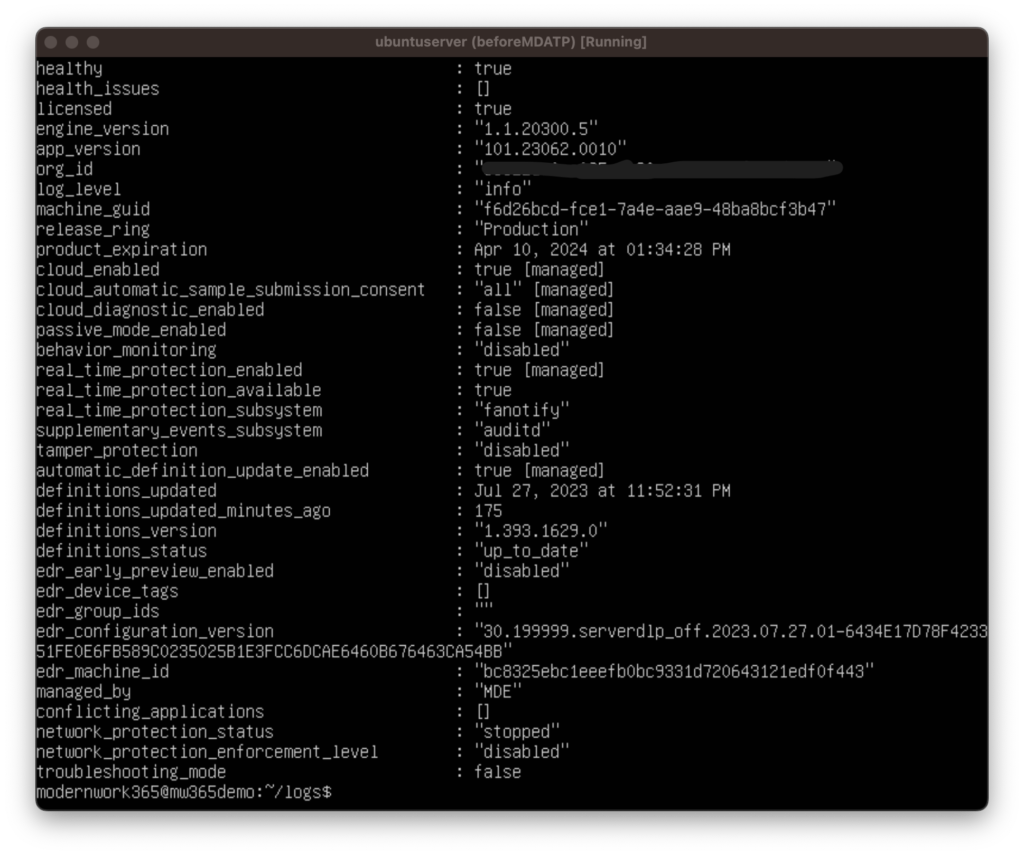
On the system we can see the server has the “managed_by” value along with the [managed] value on the settings being enforced by MDE.
Dashboards
The Microsoft 365 Defender Portal has basic dashboards that include what clients are getting setting management over what management type This is a nice addition as prior to MDE Attach on Linux or macOS, you typically replied on your Workplace or Server teams to audit if a system had a configuration or not.
In the M365 Defender Portal navigate to Endpoints > Dashboard and we can see the client health relating to MDE Attach, and what systems failed onboarding.
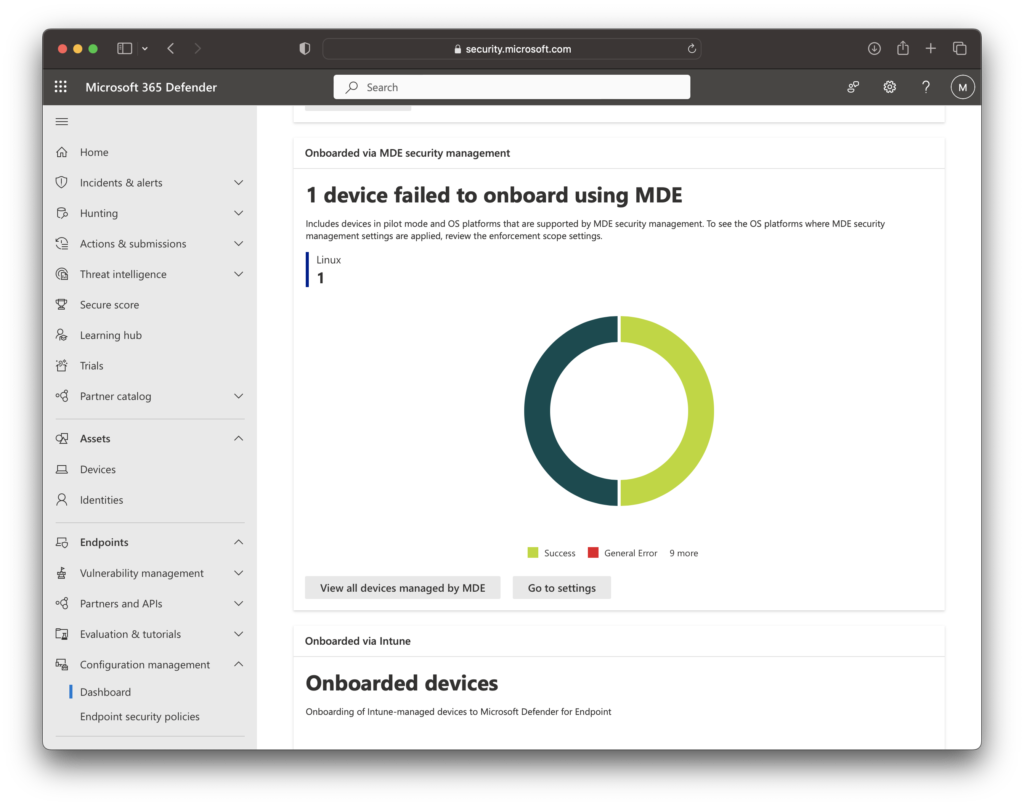
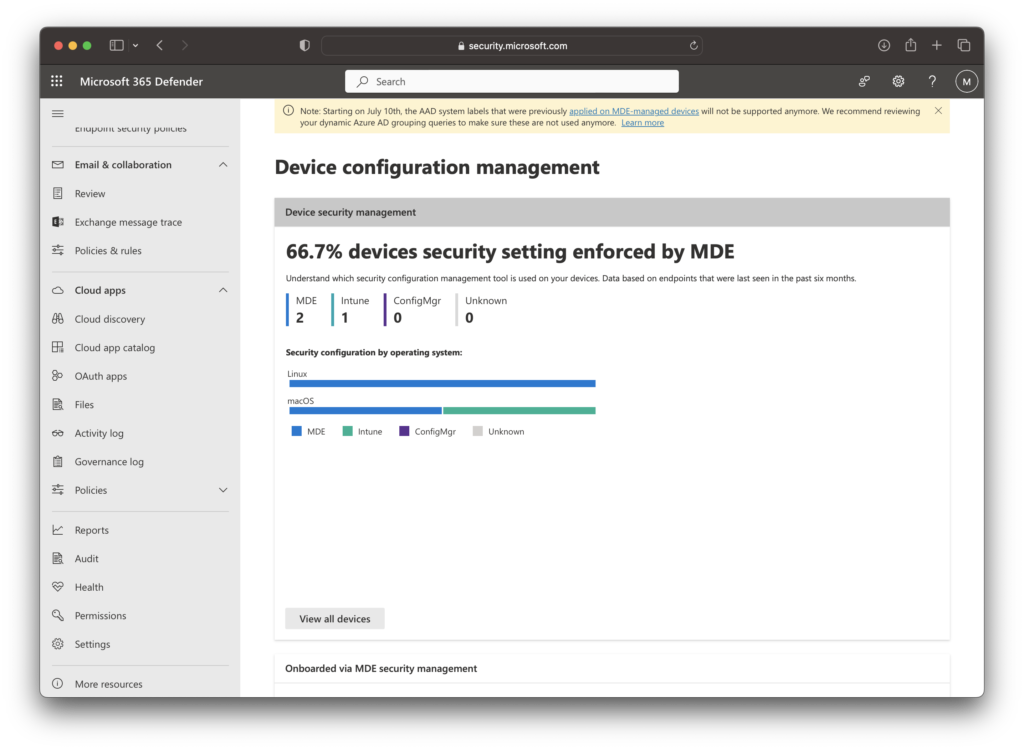
Final Thoughts
Microsoft 365 Defender
-
- For the period of Public Preview, you will also need to enable Preview Features. If this is not already enabled in your tenant, you may need to wait up to 12 hours for the feature to complete deployment to your tenant.
Entra ID Notes:
-
- Supported Topologies are not currently published, however the device requires a relationship with a single Entra ID and M365D Tenant. If you have complex identity needs due to merger, acquisitions, or divestitures, MDE Attach will not support this. I tested a scenario where a Mac was already Entra ID Registered to another Tenant and ran an onboarding package from a separate Tenant. This resulted in a Tenant Mismatch error in M365D Portal device object.
-
- Currently Entra ID shows MDE Attach as a Join Type of null in the Entra Admin Center. If a device attempts a full Entra ID Join, or Entra ID Registration as part of a user action (Entra ID Registration) the Syntenic Registration is replaced by the join type the user completed.
-
- If you want to leverage Dynamic Groups in Entra to control rollout leverage the below syntax
-
- device.deviceOSType -eq “Linux”) and (device.managementType -eq “MicrosoftSense”)
-
- (device.deviceOSType -eq “macOS”) and (device.managementType -eq “MicrosoftSense”)
-
- If you want to leverage Dynamic Groups in Entra to control rollout leverage the below syntax
Intune Notes
-
- Policy can be authored for MDE in the Intune Admin Center for macOS and Linux just like Windows today. Policies created in either portal are reflected in both portals. It does not matter where you author them.
-
- Review your RBAC model in Intune and M365D. Remember to apply model of “least privilege” to your mapping of roles to the controls in the portals.
-
- Removing a Device object in Intune Admin Center prior to offboarding in MDE will cause the agent to perform a new Synthetic Registration. Offboard the client first in MDE.
Endpoint Notes:
-
- If you are using tooling like Ansible, Chef or Puppet, ensure you decommission any pipelines or actions in your deployment process to copy the mdatp_managed.json file to new or existing Virtual Machines.
-
- Test using the “MDE-Managment” tag first!
-
- SenseCM on macOS is located in wdavdaemon_enterprise.app within the Microsoft Defender.app bundle installed in /Applications.
-
- SenseCM is located in /opt/microsoft/mdatp/sbin/ – This location may vary depending on the distribution you use.
-
- On macOS and Linux the mdatp_config.txt generated by the Client Analyzer has a number of key elements to look at including “securityManagement “, “mLastCheckinAttemptInFileTime” mLastcheckinSuccessfulInFileTime”.
- From my testing both platforms seem to leverage the existing management framework, Linux using the mdatp_managed.json deployed to /etc/opt/microsoft/mdatp/managed/ and on macOS com.microsoft.wdav.plist deployed to /Library/Managed Preferences/. SenseCM is just handling the CRUD actions.
-
- If you are using Defender for Cloud you should consider enabling “Security settings management for Microsoft Defender for Cloud onboarded devices”. This will ensure Servers onboarded thru MDC or Azure Arc connected VMs will become MDE Attach as well.

